Introduction
Imagine managing hundreds, if not thousands, of endpoints across a globally dispersed workforce. Laptops, mobile devices, servers, and cloud-based systems are all potential targets for cyber threats. If you’re an IT administrator, security team lead, or compliance officer, you know that keeping these endpoints secure is a non-stop challenge.
The stakes have never been higher. Ransomware attacks surged by 95% in 2025, and remote work has expanded the attack surface dramatically. Without a solid IT Service Management (ITSM) security strategy, organizations risk data breaches, compliance violations, and operational downtime.
Key Challenges in Endpoint Security
Here’s why endpoint security is now a critical business priority:
- Rise of Cyber Threats: Cybercriminals increasingly exploit vulnerabilities in unmanaged endpoints. Attacks like ransomware, phishing, and zero-day exploits are more sophisticated than ever.
- Remote & Hybrid Workforces: Employees are accessing sensitive data from personal devices and unsecured networks. Without centralized device monitoring and security policies, IT teams struggle to maintain control.
- Regulatory Compliance Pressure: Strict laws like ISO 27001, HIPAA, and GDPR demand end-to-end device security and comprehensive activity logging. Non-compliance can lead to hefty fines and reputational damage.
- Complex IT Infrastructures: With a mix of on-premise, cloud, and hybrid environments, organizations must secure assets across multiple platforms without adding management complexity.
🚨 Without a proactive ITSM strategy, your endpoints become the weakest link in your security framework. That’s where ITSM solutions like NinjaOne, Freshservice, and Monday Service come in.
How ITSM Enhances Endpoint Security
Traditional security tools alone aren’t enough. ITSM platforms are now essential for managing and securing endpoints at scale. They provide a centralized hub to monitor, automate, and enforce security policies across every device in your network.
1. Centralized Device Management
You can’t secure what you can’t see. ITSM platforms offer a single-pane-of-glass view of every endpoint, whether it’s a Windows laptop, Mac workstation, Linux server, or IoT device.
✔ Unified Asset Inventory: Automatically discover and catalog all endpoints in your environment.
✔ Real-Time Device Health Monitoring: Identify malware infections, failed patches, or unauthorized access attempts in real-time.
✔ Remote Troubleshooting: IT teams can investigate and resolve security issues without needing physical access to devices.
2. Automated Patch Management
Unpatched vulnerabilities account for 60% of security breaches. Manually tracking software updates is inefficient and risky. ITSM automates the process to ensure all endpoints stay updated.
- Zero-Touch Patch Deployment: Deploy security updates automatically across Windows, Mac, and Linux systems.
- Scheduled & On-Demand Patching: Set predefined patch cycles or push emergency updates when a new vulnerability is discovered.
- Patch Compliance Reports: Get audit-ready reports showing which endpoints are patched and which need attention.
3. Incident Response & Monitoring
When a security breach happens, time is critical. ITSM tools provide real-time alerting and automated incident workflows to minimize damage.
- Automated Alerts: Get instant notifications for suspicious activities, unauthorized logins, or malware infections.
- Predefined Response Workflows: Automate threat containment by isolating infected devices and revoking access if needed.
- Audit Logs for Compliance: Maintain detailed logs for forensic investigations and regulatory compliance audits.
4. Endpoint Compliance & Configuration Management
Ensuring security isn’t just about stopping attacks, it’s also about proving compliance to auditors and stakeholders.
✔ Configuration Baselines: Standardize security settings across all endpoints to meet compliance standards.
✔ Role-Based Access Controls: Restrict access based on user roles to prevent unauthorized data access.
✔ Data Encryption & Backup: Ensure sensitive data is encrypted in transit and at rest while maintaining secure backups for disaster recovery.
✅ Compare ITSM Solutions in Our Full Guide
Managing Devices at Scale with ITSM Solutions
Scaling endpoint security isn’t just about adding more tools; it’s about integrating security into IT operations efficiently. The right ITSM platform helps you manage thousands of devices without overwhelming your IT team.
In this section, we’ll explore how NinjaOne, Freshservice, and monday service enable IT admins, security teams, and compliance officers to secure, monitor, and manage endpoints at scale.
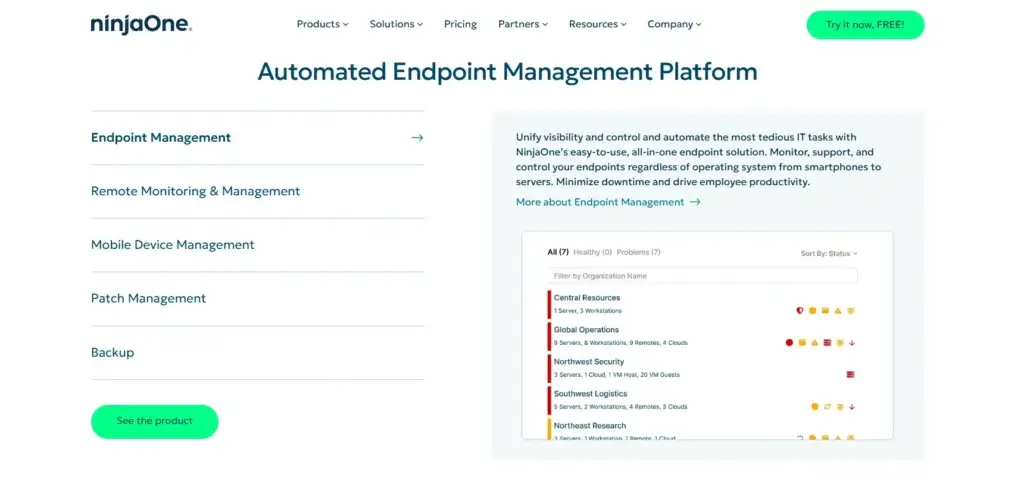
Why IT Teams Choose NinjaOne:
✔ Automated Patch Management to close security gaps before attackers exploit them.
✔ Cloud-native remote monitoring to secure Windows, Mac, and Linux devices from anywhere.
✔ Endpoint Detection & Response (EDR) powered by BitDefender & SentinelOne for advanced threat protectionNinjaOne_RMM Handout.
Key Security Features
Full Endpoint Visibility:
- Discover and track all devices across on-premise, cloud, and hybrid environments.
- Set real-time alerts for suspicious activity.
Automated Security Compliance:
- Pre-configure security baselines to meet ISO 27001, HIPAA, and GDPR requirements.
- Keep audit logs to prove compliance.
Fast & Secure Remote Access:
- IT admins can securely troubleshoot issues without requiring user intervention.
- Encrypted remote sessions protect sensitive data from interception.
💡 Best For:
- IT teams need scalable, automated security for diverse device environments.
- Companies that want seamless patching & compliance reporting in one platform.
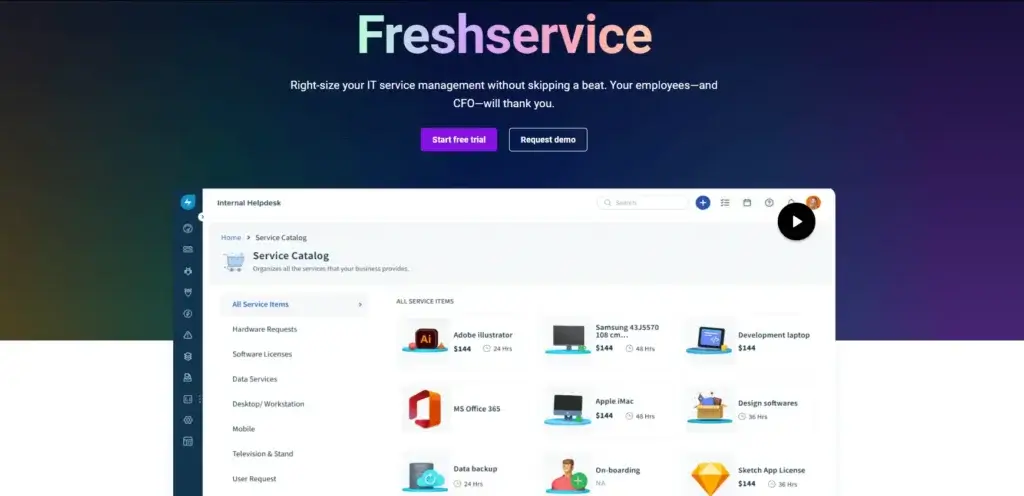
Why IT Teams Choose Freshservice:
✔ IT Asset Management (ITAM) for full endpoint tracking and security auditing.
✔ Incident Response Automation to contain security threats faster.
✔ Change & Configuration Management to ensure secure device provisioning.
Key Security Features
Automated Risk Mitigation:
- AI-powered security workflows instantly respond to potential breaches.
- Automated patching with vulnerability scanning prevents exploitation.
Proactive Security Monitoring:
- Role-based access control (RBAC) restricts unauthorized endpoint access.
- Automated compliance checks ensure all devices meet regulatory standards.
Deep Endpoint Insights & Audits:
- The Configuration Management Database (CMDB) maintains a centralized record of all endpoint security changes.
- Customizable security policies enforce encryption, firewall, and VPN usage.
💡 Best For:
- Organizations look for a strong blend of ITSM and security automation.
- IT security teams need audit-friendly device management.
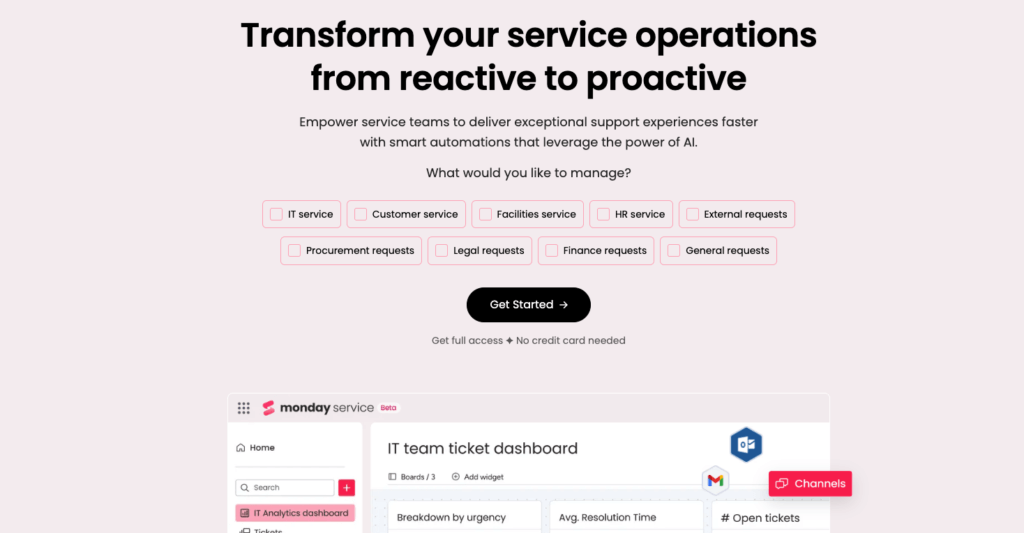
Why IT Teams Choose Monday Service:
✔ Customizable IT workflows for endpoint security monitoring.
✔ Incident response automation to minimize security threats.
✔ User-friendly dashboards for real-time endpoint status tracking.
Key Security Features
Centralized Device Monitoring:
- View all endpoint security metrics in one dashboard.
- Detect misconfigured or non-compliant devices instantly.
Security-Focused Automation:
- Trigger automatic security actions (e.g., force logout, revoke access, enforce patching).
- Custom security workflows to tailor compliance enforcement.
Seamless Integration with IT Tools:
- Connects with SIEM, antivirus, and vulnerability management solutions.
- Automates ticket escalation for security incidents.
💡 Best For:
- IT teams look for a highly customizable yet easy-to-use security solution.
- Businesses need real-time security insights with automation.
Comparison Table
| Feature | NinjaOne | Freshservice | monday service |
| Automated Patch Management | Yes – Full automation with zero-touch patching | Yes – AI-driven patch automation | No – Requires third-party integration |
| Endpoint Monitoring & Visibility | Yes – Real-time alerts and full asset inventory | Yes – Asset tracking with CMDB integration | Yes – Dashboard-based endpoint monitoring |
| Integrated Security Tools | Yes – BitDefender & SentinelOne EDR | Yes – Security workflows and risk mitigation | No – Relies on external security tools |
| Compliance & Audit Logging | Yes – Compliance-ready audit logs | Yes – Audit-friendly compliance management | Yes – Customizable compliance policies |
| Incident Response Automation | Yes – Automated security response workflows | Yes – AI-powered risk response automation | Yes – Automated security ticket escalation |
| Remote Access Security | Yes – Encrypted remote sessions | No – Requires third-party integrations | No – Basic access control only |
| Customization & Workflow Automation | Moderate – Pre-configured policies and scripting | High – Fully customizable security workflows | Very High – Fully customizable ITSM workflows |
| Best For | IT teams are looking for a highly customizable, user-friendly security solution | Organizations requiring ITSM-driven security automation and compliance | IT teams looking for a highly customizable, user-friendly security solution |

Best Practices for ITSM-Driven Endpoint Security
Implementing endpoint security at scale requires more than just tools; it demands a strategic approach that integrates ITSM best practices. Here’s how you can strengthen your endpoint security posture with IT Service Management solutions.
Implement a Zero-Trust Security Framework
The traditional “trust but verify” model is obsolete. Instead, zero-trust security ensures that no device or user is inherently trusted.
- Enforce strict access controls – Only allow verified users and devices to access critical systems.
- Monitor endpoint behavior continuously – Flag anomalies in login locations, unusual software installations, or unauthorized file transfers.
- Utilize multi-factor authentication (MFA) – Reduce the risk of compromised credentials.
- Network segmentation – Isolate high-risk devices from sensitive assets to limit the spread of threats.
🚀 How ITSM Helps:
- NinjaOne enables automated policy enforcement to ensure all endpoints meet security standards.
- Freshservice offers role-based access control (RBAC) to restrict unauthorized access.
- Monday Service allows IT teams to set custom security workflows for user authentication.
Automate Patch Management to Reduce Vulnerabilities
Patch delays are a leading cause of security breaches. Manually updating systems is impractical; automation is the key.
- Deploy patches organization-wide without waiting for manual approvals.
- Test patches in a controlled environment before rolling them out to production devices.
- Schedule automated updates outside peak hours to minimize disruptions.
- Monitor patch status across all endpoints to ensure compliance.
🚀 How ITSM Helps:
- NinjaOne offers zero-touch patching that updates Windows, Mac, and Linux systems seamlessly.
- Freshservice uses AI-powered patch automation to detect and fix vulnerabilities.
- Monday Service relies on third-party integrations for patching but allows IT teams to track compliance.
Strengthen Incident Response with ITSM Automation
When a security threat is detected, speed is critical. Automating response workflows minimizes human error and ensures swift containment.
- Set up real-time alerts for unusual activities (e.g., unauthorized logins, malware detection).
- Automate threat containment – isolate infected devices immediately.
- Predefine escalation workflows to involve security teams when high-risk incidents occur.
- Maintain detailed audit logs for forensic investigations and compliance reporting.
🚀 How ITSM Helps:
- NinjaOne provides real-time security alerts with automated ticketing.
- Freshservice integrates AI-driven incident response to automatically contain security breaches.
- Monday Service supports incident tracking and escalation workflows for faster response.
Integrate ITSM with SIEM & Endpoint Protection Solutions
Standalone ITSM solutions are powerful, but integrating them with security information and event management (SIEM) tools strengthens endpoint protection.
- Collect security logs from ITSM and SIEM systems to correlate threats.
- Enable automated threat intelligence sharing between IT and security teams.
- Use AI-driven analytics to detect patterns and predict cyberattacks.
🚀 How ITSM Helps:
- NinjaOne supports integration with EDR solutions like SentinelOne.
- Freshservice provides API-based integrations with SIEM and security tools.
- Monday Service enables custom integrations for security monitoring through its ITSM workflows.
Ensure Regulatory Compliance with ITSM Security Policies
Failure to comply with security regulations can lead to fines, lawsuits, and reputational damage. ITSM plays a crucial role in maintaining compliance across all endpoints.
- Enforce security configurations that align with ISO 27001, HIPAA, and GDPR.
- Conduct regular security audits to identify compliance gaps.
- Automate compliance reporting to simplify regulatory documentation.
🚀 How ITSM Helps:
- NinjaOne maintains compliance-ready audit logs for endpoint security.
- Freshservice provides predefined compliance workflows for risk assessment.
- Monday Service enables custom compliance tracking through automation.
Final Thoughts
Endpoint security is no longer optional; it’s an essential business strategy. By integrating ITSM with security automation, IT teams can scale endpoint protection, reduce cyber risks, and ensure compliance effortlessly.
✅ For full automation and compliance tracking, go with NinjaOne.
✅ If you need AI-driven automation with deep security workflows, choose Freshservice.
✅ For flexible, customizable security workflows, consider Monday Service.
As cyber threats continue to evolve, staying ahead means embracing ITSM-powered security. Start automating your endpoint security today and build a resilient, future-proof IT environment.
✅ Compare ITSM Solutions in Our Full Guide
FAQ
What is Endpoint Security in ITSM?
Endpoint security in IT Service Management (ITSM) focuses on protecting and managing devices connected to an organization’s network, like laptops, mobile phones, desktops, and servers. ITSM platforms help automate patching, enforce security policies, and ensure compliance with industry standards such as ISO 27001, HIPAA, and GDPR.
Why is ITSM Important for Endpoint Security?
ITSM centralizes endpoint control, which is essential for scaling security in modern environments. It enables real-time monitoring, automates patching to fix vulnerabilities, and enforces compliance policies across all devices. With predefined workflows, IT teams can quickly respond to security incidents, reducing the risk of breaches.
Which ITSM Tools Offer the Best Endpoint Security Features?
Top ITSM tools like NinjaOne, Freshservice, and monday service stand out for endpoint protection. NinjaOne includes automated patching and built-in EDR, Freshservice offers AI-powered risk mitigation and asset management, while Monday Service allows customizable security workflows and real-time incident escalation. The right choice depends on your organization’s specific needs.
How Does ITSM Help With Automated Patching?
ITSM platforms streamline patching by automating deployment across all endpoints. This includes scheduled updates, emergency patches for zero-day threats, and compliance tracking through detailed reporting. Solutions like NinjaOne and Freshservice minimize manual intervention, closing security gaps quickly and reliably.
Can ITSM Help Prevent Ransomware Attacks?
Yes, ITSM is a critical layer in ransomware defense. It ensures systems stay updated, enforces access controls, and uses endpoint monitoring to detect unusual behavior. Many tools, like NinjaOne and Freshservice, integrate with advanced threat detection platforms and automate incident response to contain attacks fast.
Can ITSM Manage Remote & Hybrid Workforces Securely?
Modern ITSM solutions are built for remote work. They provide full visibility into remote devices, enforce security policies regardless of location, and support automated patching from the cloud. Tools like NinjaOne, Freshservice, and Monday Service also include secure remote access tools, making them ideal for hybrid environments.