
Secure Private Access is becoming the go-to solution for organizations looking to move beyond legacy VPNs. If you’re managing remote teams or hybrid environments, you need a security model that limits risk without limiting productivity.
In this guide, you’ll learn exactly what Secure Private Access is, how it works, and why leading companies are adopting it to replace traditional network access methods. We’ll also walk through practical use cases, compare major vendors like Citrix and Zscaler, and provide a high-level setup overview.
Whether you’re an IT decision-maker or security lead, this guide will help you build a more secure, scalable access strategy for 2025 and beyond.
What Is Secure Private Access?
Secure Private Access (SPA) is a modern security model that allows users to access internal apps and resources without exposing the entire network. Unlike VPNs, which often provide broad network-level access, SPA uses identity-based, policy-driven controls to enforce application-specific access.
This approach is rooted in Zero Trust principles, which means users never implicitly “trust” the network just because they’re connected. Every access request is verified, authorized, and logged.
🔍 Why Traditional VPNs Fall Short
VPNs served a purpose when everyone worked from the office or occasionally dialed in remotely. But in today’s cloud-first, hybrid world, they come with serious limitations:
- Broad access to the entire network, increasing attack surface
- Performance issues with SaaS and cloud-based applications
- Complex scaling for remote workforces
- Lack of context-aware, granular access controls
If you’ve struggled with sluggish connections or over-provisioned access via VPN, you’re not alone. That’s why companies are moving toward Secure Private Access and ZTNA models.
What Makes Secure Private Access Different?
SPA flips the script on traditional network access. Instead of connecting users to the network, it connects users directly to the specific applications they’re authorized to use, nothing more.
Key traits include:
- Application-level access: No lateral movement across the network
- Identity-driven permissions: Access based on user, device, and context
- Brokered connections: Users never connect directly to backend apps
- Cloud-native scalability: Easily support global users without on-prem hardware
These features make SPA ideal for hybrid teams, third-party contractors, and BYOD environments.
Zero Trust Network Access (ZTNA) Explained
Secure Private Access is often regarded as a practical application of Zero Trust Network Access (ZTNA). In a ZTNA model:
- Every session is authenticated and authorized in real time
- Access policies are enforced dynamically based on identity and context
- Resources are hidden unless explicitly allowed
ZTNA is now considered the future of secure remote access. By 2025, most enterprise-grade security strategies are expected to adopt some form of Zero Trust architecture, with SPA being a foundational component.
Secure Private Access Architecture
Understanding how SPA works under the hood is key to a successful implementation. While each vendor may use different terminology, most Secure Private Access systems follow a similar architecture.
Core Components of Secure Private Access
Every SPA solution generally includes the following components:
- Endpoint Agent or Client: Installed on the user’s device to initiate secure requests
- Cloud Broker or Controller: Mediates connections between users and apps
- Application Connector: Deployed in your network or cloud to create outbound-only links
- Policy Engine: Applies granular access rules based on identity, device posture, location, etc.
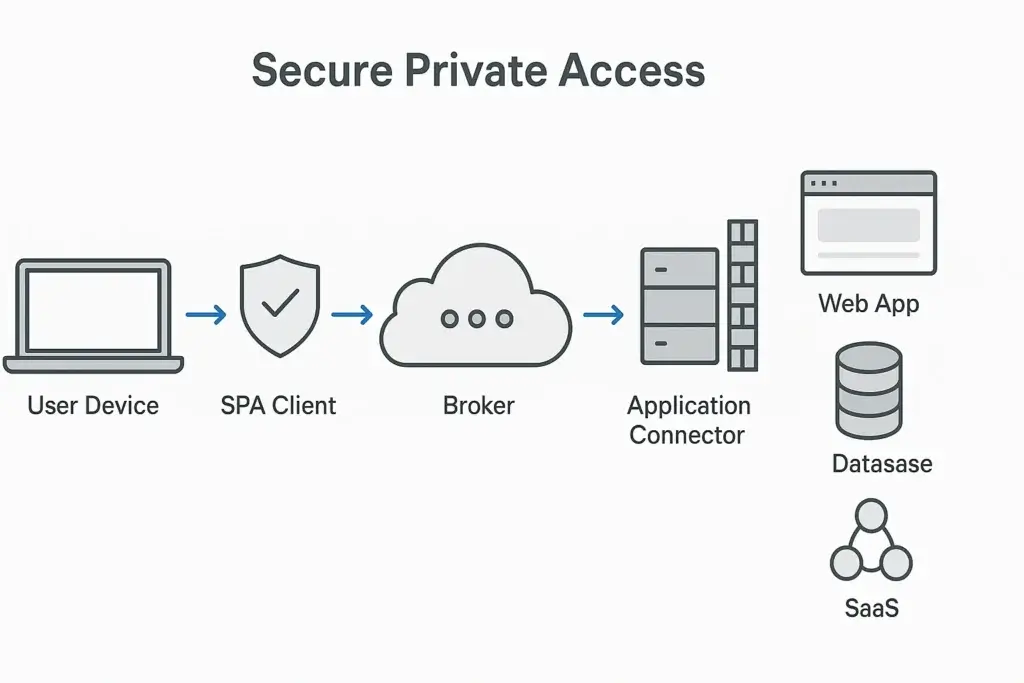
How It Works: End-to-End Flow
Here’s a simplified look at how most platforms, like Citrix Secure Private Access, connect a user to a private application:
- User logs in via SPA client with multi-factor authentication
- The broker verifies identity, device health, and access policy
- If approved, a temporary app-specific connection is established via the connector
- The user connects only to that app, no network-level access is granted
This flow ensures that apps remain hidden and inaccessible unless explicitly permitted. It also reduces the chances of lateral movement or privilege escalation.
Secure Private Access vs VPNs
Let’s break down how SPA compares with traditional VPNs:
| Feature | Secure Private Access | Traditional VPN |
| Access Scope | App-level only | Full network access |
| Security Model | Zero Trust | Implicit trust |
| Deployment | Cloud-native | Appliance-based |
| User Experience | Fast, seamless | Slower, clunky |
| Scalability | High (global) | Limited (on-prem) |
Use Cases and Benefits of Secure Private Access
Secure Private Access isn’t just a replacement for VPNs, it’s a strategic enabler for modern IT environments. Whether you’re supporting remote employees, securing third-party access, or managing hybrid infrastructure, SPA helps you strike the right balance between control and convenience.
Let’s explore where it fits best and why it’s gaining so much traction in 2025.
🔐 Private App Access Without VPN
If you’re dealing with internal web apps, databases, or custom tools hosted on-prem or in the cloud, Secure Private Access gives your team a direct and secure way to reach them, without ever connecting to the broader network.
Common scenarios include:
- Developers accessing Git, Jenkins, or internal APIs
- HR teams logging into private portals
- Finance teams working with on-prem accounting tools
SPA ensures each user only reaches the apps they’re authorized to use. Everything else remains invisible.
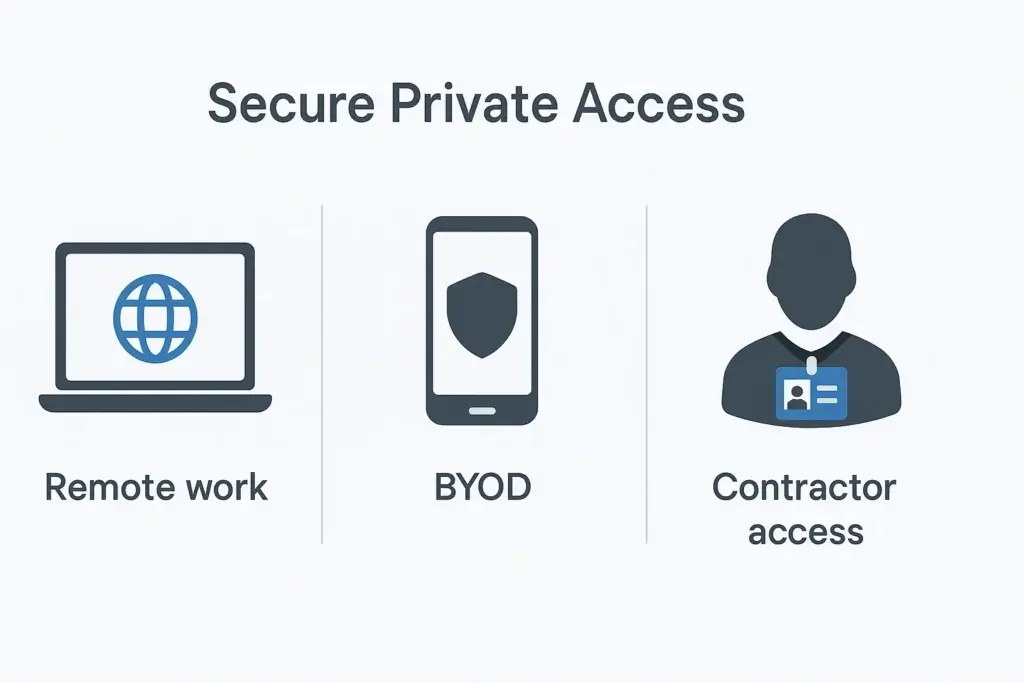
Supporting Remote Work and BYOD Environments
Traditional VPNs struggle with remote and bring-your-own-device (BYOD) setups because they assume trust once a connection is made.
With SPA, you can:
- Grant app-level access from unmanaged devices
- Enforce device posture checks (e.g., antivirus status, OS version)
- Support hybrid workers without opening up your entire network
This flexibility makes Secure Private Access ideal for distributed teams in 2025, especially as remote-first policies become the norm.
SPA can complement work management tools by adding secure access to internal systems.
Enabling Third-Party and Contractor Access
Let’s say you’ve hired a freelance developer or outsourced support. Giving them a VPN account can be risky and hard to revoke later.
SPA solves this by letting you:
- Create temporary, app-specific access profiles
- Avoid provisioning full user credentials or VPN tunnels
- Monitor and log access with detailed session data
You maintain visibility and control without compromising security.
Key Benefits of Secure Private Access
Here’s a quick look at what you gain when implementing SPA in your environment:
- ✅ Minimized attack surface: No open ports or exposed IPs
- 🔐 Granular access control: Permissions down to the app and user level
- 💡 Improved user experience: No more full VPN tunneling or latency
- 📈 Scalable architecture: Built for global teams and cloud growth
- 🧩 Vendor-neutral flexibility: Compatible with ITSM tools like Freshservice or NinjaOne
And because SPA follows a Zero Trust model, you can layer it with existing identity providers, MFA tools, and endpoint security solutions.
How to Set Up Secure Private Access (Generic Guide)
Ready to implement Secure Private Access in your organization? This section walks you through the general process, whether you’re deploying Citrix, Zscaler, Microsoft Entra, or another provider.
The goal here isn’t to lock you into one platform but to help you understand what to expect and how to prepare your environment.
🔧 Prerequisites and System Requirements
Before you roll out SPA, make sure you’ve got the following elements in place:
- ✅ Identity provider (IdP): Such as Azure AD, Okta, or Google Workspace
- ✅ Endpoints: Company-managed or BYOD devices where the SPA client will run
- ✅ Apps to protect: Internal web apps, cloud apps, or file shares
- ✅ Network locations: On-premise or cloud-based servers that host the apps
- ✅ Security stack integrations: For posture checks, logging, or SIEM tools
📌 Tip: Start small. Roll out SPA for a single internal web app before expanding across departments.
Step-by-Step Setup Process
Here’s a simplified version of how most Secure Private Access deployments work in 2025:
- Deploy the connector in your internal network or cloud to establish outbound-only tunnels to the SPA broker.
- Install endpoint agents or browser extensions on user devices, depending on your vendor.
- Integrate with your identity provider to enforce user-based access policies.
- Define access policies by user role, device status, geolocation, or time of day.
- Assign apps to user groups so only authorized users can see and access each application.
- Test with a small user group, monitor logs, and adjust access rules as needed.
- Scale deployment, including BYOD access and third-party contractor profiles.
Each solution will have its own admin console and policy language, but these steps remain consistent across platforms.
Configuring Policies and Access Rules
This is where the real power of SPA lies: customizable policies that go beyond simple IP whitelisting or username/password logins.
Common rule types include:
- User identity and role (from IdP)
- Device health checks (e.g., OS version, antivirus, MDM status)
- Location restrictions (block access from specific geographies)
- Time-based access (e.g., only during business hours)
- Session logging and alerts (for compliance and audit purposes)
With Secure Private Access, you’re no longer handing out the keys to the entire network. Instead, you define exactly who can access what and under what conditions.
Vendor Comparison: Citrix vs Zscaler vs Microsoft Entra
If you’re exploring Secure Private Access solutions in 2025, chances are these three names have come up. Each vendor takes a slightly different approach, but all aim to deliver a Zero Trust, app-centric access model.
Use this comparison to understand key differences and choose what works best for your environment.
🔍 Overview of Each Solution
- Citrix Secure Private Access: Focused on enterprise-grade app delivery, VDI, and hybrid environments.
- Zscaler Private Access (ZPA): Cloud-native ZTNA platform built for simplicity, SaaS, and remote users.
- Microsoft Entra Private Access: Part of Microsoft’s Zero Trust stack, tailored for organizations using Microsoft 365 and Azure ecosystems.
🔄 Feature Comparison Table
| Feature | Citrix SPA | Zscaler ZPA | Microsoft Entra |
| ZTNA Support | Yes, full | Yes, advanced | Yes, integrated |
| Application Connector | Citrix Connector | Zscaler App Connector | Global Secure Access Client |
| SSO Integration | Works with Okta, Azure AD, etc. | Broad SSO support | Tight integration with Entra ID |
| Deployment Complexity | Medium (on-prem or hybrid) | Low (cloud-first) | High (PowerShell, Intune) |
| Best For | VDI & legacy app environments | Cloud-first orgs & SaaS access | Microsoft 365-based enterprises |
| Policy Customization | Role-based access, app-layer controls | Highly granular, policy engine built-in | Conditional Access + Defender integration |
| Logging & Visibility | Via Citrix Analytics | Full logging with SIEM support | Azure Monitor & Sentinel |
🧩 Choosing the Right Fit for Your Business
Still unsure which one to go with? Here’s a simplified way to think about it:
-
Choose Citrix if you already use Citrix VDI or have complex hybrid environments that include legacy apps and on-prem infrastructure.
-
Choose Zscaler if you want a lightweight, cloud-native solution that supports fast rollout for remote users, contractors, and SaaS environments.
-
Choose Microsoft Entra if your stack is already built around Microsoft tools and you’re ready to handle the steeper learning curve for advanced conditional access.
💡 Tip: Zscaler ZPA is often the easiest to start with, while Citrix and Microsoft offer deeper integration for more complex enterprise needs.
Security and Compliance Considerations
When you implement Secure Private Access, you’re not just improving connectivity; you’re making a strategic move to strengthen your organization’s security posture.
Here’s what you need to know about encryption, access controls, and compliance readiness.
🔐 Encryption and Data Protection
Modern Secure Private Access solutions encrypt all data in transit using TLS 1.2 or higher. But encryption alone isn’t the full story.
What sets SPA apart:
- No open inbound ports: Connectors initiate outbound-only tunnels, reducing attack surface
- Hidden infrastructure: Apps and services remain undiscoverable unless access is granted
- App segmentation: Prevents lateral movement and isolates sensitive environments
- End-to-end encryption: Data flows are encrypted from device to application
These design principles align with Zero Trust, ensuring every connection is both authenticated and authorized before it happens.
Identity-Based Access and Session Control
Unlike VPNs that operate on network-level access, SPA applies security controls at the identity and session layer.
You can enforce:
- Access by role (e.g., developer, HR, contractor)
- Context-aware controls like device health, geolocation, or time of day
- Re-authentication or step-up MFA for sensitive applications
- Session time limits, logging, and real-time alerting
These controls drastically reduce the risk of unauthorized access, even from compromised credentials.
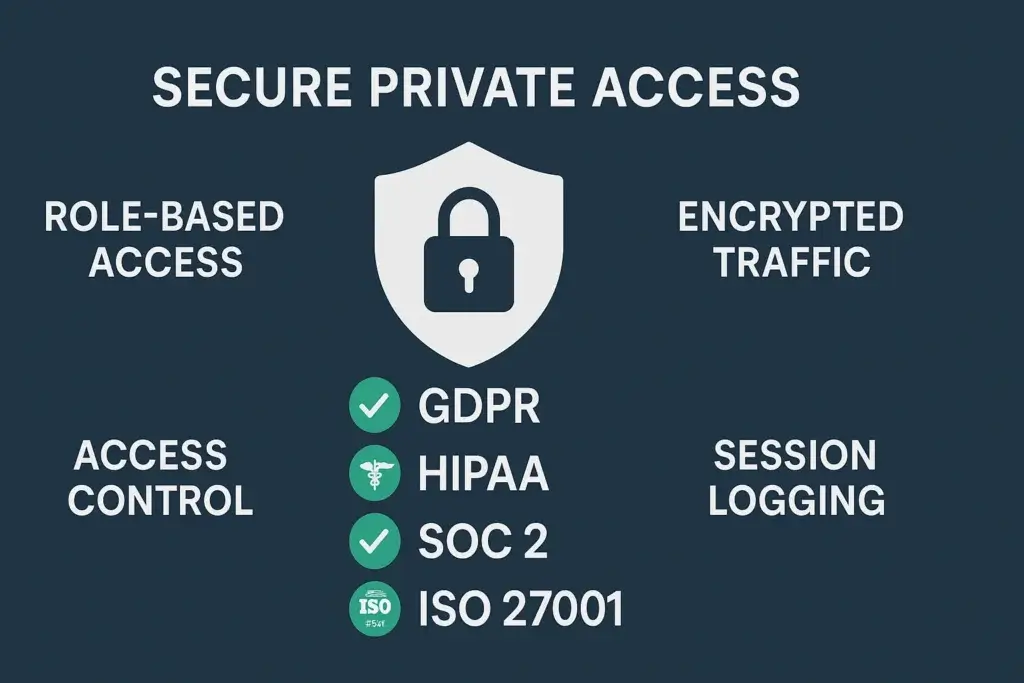
Meeting Compliance Standards in 2025
Secure Private Access helps you stay aligned with major security frameworks and regulations, including:
- GDPR – Keep data flows encrypted and access restricted by region or user role
- HIPAA – Ensure only approved staff access health records with full session logging
- SOC 2 Type II – Prove access control, monitoring, and response measures
- ISO/IEC 27001 – Centralize identity policies and access governance
If your industry is regulated, you’ll benefit from SPA’s audit-ready architecture and centralized policy enforcement.
💡 Tip: Look for SPA vendors that offer prebuilt compliance templates or integrations with tools like Microsoft Defender, Splunk, or CrowdStrike.
Final Words: Why It Matters in 2025
In 2025, Secure Private Access is no longer a nice-to-have; it’s a core part of a modern cybersecurity strategy.
If you’re still relying on VPNs, you’re likely sacrificing performance, scalability, and control. SPA gives you:
- Application-specific access
- Identity-driven policies
- Stronger compliance posture
- Better user experience
You don’t need to rip out your entire network or start from scratch. Most SPA solutions integrate with your existing identity provider, security tools, and infrastructure.
Whether you choose Citrix, Zscaler, Microsoft Entra, or a combination, make sure your team is protected with access that’s smart, secure, and scalable.
Frequently Asked Questions (FAQs)
What is Secure Private Access?
Secure Private Access (SPA) is a Zero Trust model that allows users to access specific internal apps without exposing the entire network.
How is Secure Private Access different from VPN?
SPA grants access at the application level, while VPNs open the full network. SPA also uses identity-based policies for better control and security.
What are the key components of SPA architecture?
Most setups include an endpoint agent, cloud broker, application connector, and policy engine.
Can Secure Private Access replace my VPN entirely?
In many cases, yes, especially if you’re managing remote teams, contractors, or hybrid cloud environments.
Is SPA secure enough for regulated industries?
Yes. It supports GDPR, HIPAA, SOC 2, and other standards by enforcing encrypted, role-based access.
Which vendors offer SPA solutions?
Leading providers include Citrix (SPA), Zscaler (ZPA), and Microsoft Entra Private Access.
Do I need to install software on user devices?
Most vendors require either a lightweight agent or a browser-based client for policy enforcement.
How long does deployment take?
Small deployments can be done in days. Full enterprise rollouts depend on your infrastructure and the number of users.
Does SPA work with BYOD or unmanaged devices?
Yes, many solutions support posture checks and risk-based access for personal or unmanaged endpoints.
Is Secure Private Access expensive?
Pricing varies, but cloud-native platforms tend to be more cost-effective and easier to scale than traditional VPN appliances.






